A recent paper published in the journal Sensors introduces a novel approach to cooperative attack detection within the Internet of Things (IoT) using black hole optimization (BHO) and convolutional neural networks (CNN).
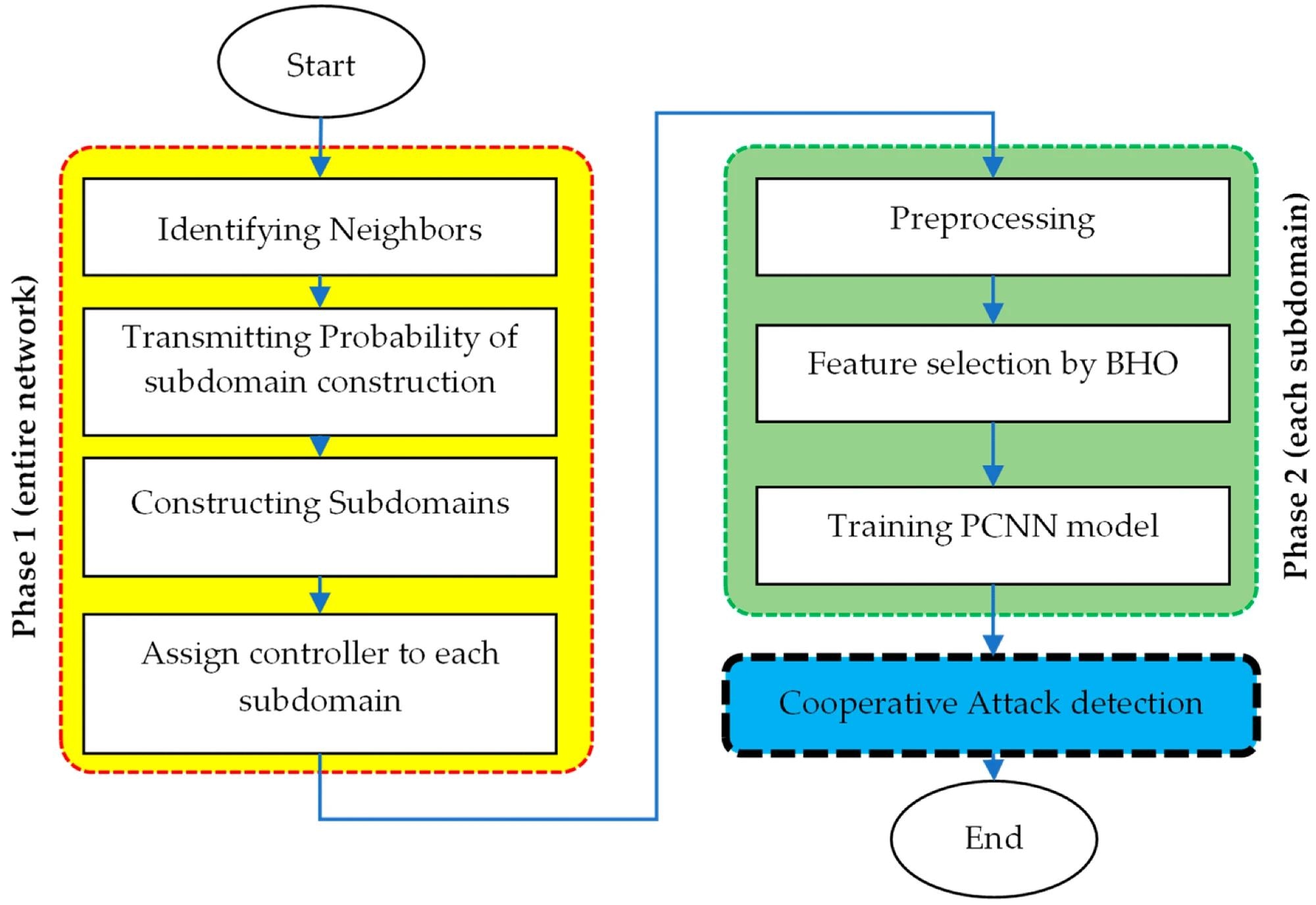 The steps of the proposed method. Image Credit: https://www.mdpi.com/1424-8220/24/15/4766
The steps of the proposed method. Image Credit: https://www.mdpi.com/1424-8220/24/15/4766
IoT Security Challenges
Ensuring security in communication networks has consistently been a major concern. The IoT has become a particularly critical issue due to the security challenges associated with delicate IoT applications. In real-world scenarios like industrial IoT or smart cities, a successful network breach by attackers and their subsequent control over the functionality of connected objects can cause irreversible harm.
Although IoT security has garnered significant attention from researchers, recent studies indicate that previously proposed solutions are not adequately effective. The security issue is becoming increasingly complicated due to the rapid emergence of new attack types and the development of advanced intrusion techniques. One effective computer network security solution is the intrusion detection system (IDS), which identifies attacks through pattern analysis.
Currently, several IDSs are available for IoT due to their ease of integration and implementation within IoT environments. However, most of the previous models used centralized systems for threat identification. These centralized topologies can increase network vulnerabilities, communication overheads, and costs, rendering them ineffective. Additionally, most previous decentralized techniques have worse detection accuracy compared to centralized models.
The Study
In this study, the researchers proposed a cooperative and novel approach to IoT intrusion detection to effectively resolve existing security issues. This cooperative IDS architecture aims to lower communication overhead and cost in the intrusion detection process while simultaneously addressing IoT vulnerability issues.
The proposed approach utilizes BHO to select the most relevant attributes that effectively describe communication between objects. Specifically, this BHO-based feature selection technique identifies the smallest number of features necessary to represent an object’s communication, minimizing training error.
Additionally, a novel matrix-based method was introduced to describe the network’s communication properties. The proposed intrusion detection model's inputs consisted of these two feature sets. The network was divided into multiple subnets using a software-defined network (SDN).
Each subnet was monitored by a controller node that employed a parallel CNN (PCNN) combination to detect security threats within the traffic passing through its subnet. In this PCNN-based IoT local attack detection architecture, the BHO-chosen features were processed by the first CNN, while the communication features in matrix form were processed by the second CNN.
These two CNN models' characteristics were combined, and a SoftMax layer was added to detect the presence of an attack. Each intrusion detection agent utilized the PCNN model locally in the proposed cooperative intrusion detection architecture built on SDN in the IoT. The approach also employed a majority voting mechanism for controller node cooperation to improve attack detection accuracy.
Specifically, the participating controllers communicated their local detection findings and used majority voting to identify the presence of attacks. Unlike centralized models, this majority voting approach ensures improved detection accuracy.
The study used samples from the NSLKDD and NSW-NB15 databases, which are extensively utilized in IDS applications in the IoT, to evaluate the proposed approach. The NSLKDD database addresses issues from the KDD’99 data collection, while the NSW-NB15 database covers nine forms of assaults.
Importance of this Work
Results displayed that the proposed cooperative IDS could detect assaults in the NSLKDD and NSW-NB15 datasets with high accuracy of 99.89 % and 97.72 %, respectively, which underscored the importance of BHO and PCNN combination for feature selection and classification.
Additionally, the use of both matrix and vector-based characteristics by the PCNN model enabled the model to provide a more comprehensive network traffic view for attack detection. Thus, this architecture enhanced the accuracy by at least 3.35 % when compared with the individual CNN models on both NSLKDD and NSW-NB15 datasets.
Moreover, the majority voting technique among the cooperative IDS controller nodes also increased the accuracy by 2.1 % compared to the non-cooperative detection technique, reducing the possible errors in the system’s individual nodes and thereby improving the overall IDS reliability. The proposed model also showed its superiority in more accurate threat identification when compared with hybrid approaches like CNN–HETIoT and MFE–ELM.
To summarize, this study's findings demonstrated the feasibility of using the proposed cooperative IDS for attack detection in IoT scenarios.
Journal Reference
Li, P., Wang, H., Tian, G., Fan, Z. (2024). A Cooperative Intrusion Detection System for the Internet of Things Using Convolutional Neural Networks and Black Hole Optimization. Sensors, 24(15), 4766. DOI: 10.3390/s24154766, https://www.mdpi.com/1424-8220/24/15/4766
Disclaimer: The views expressed here are those of the author expressed in their private capacity and do not necessarily represent the views of AZoM.com Limited T/A AZoNetwork the owner and operator of this website. This disclaimer forms part of the Terms and conditions of use of this website.