Nov 27 2015
Cryptography is the approach to protect data secrecy in public environment. Certain cryptographic communications require not only the security of the transmitted message against eavesdropping from an outside adversary, but also the communicators' individual privacy against each other. Symmetrically private information retrieval (SPIR), which deals with the problem of private user queries to a database, is an example of such communication protocols.
In a SPIR protocol Alice can obtain one item (i.e. one secret) from Bob's secret database in such a manner that Bob does not know which item Alice has obtained and, simultaneously, Alice cannot get additional items except the one she wanted in the database.
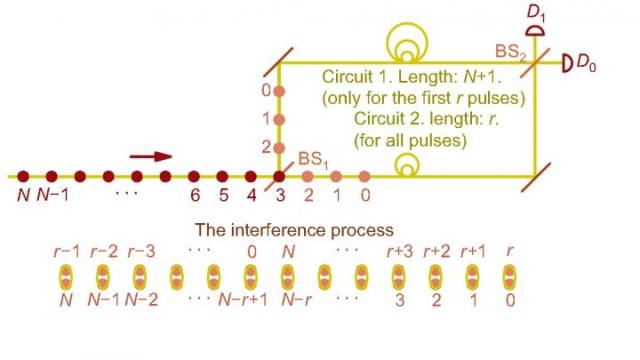 The interference wiring diagram of the newly proposed QPQ protocol, where the database generates a single-photon signal with N optical pulses and shifts the phase of each pulse randomly by 0 or ð, then the user extracts the phase differential of two pulses of them by the circuits on the right side and a random number r. CREDIT: ©science china press
The interference wiring diagram of the newly proposed QPQ protocol, where the database generates a single-photon signal with N optical pulses and shifts the phase of each pulse randomly by 0 or ð, then the user extracts the phase differential of two pulses of them by the circuits on the right side and a random number r. CREDIT: ©science china press
With the advantage of unconditional security, as we know, quantum cryptography has attracted a great deal of attention now. Quantum private query (QPQ) is the quantum scheme for SPIR problem. Since the first QPQ protocol was proposed by Vittorio Giovannetti et al in 2008, quite a few scholars have participated in the study of this interesting and important field. The original QPQ protocols are based on oracle operations. Though those protocols have significant advantages in theory, they are difficult to implement since the dimension of the oracle operation would be exceedingly high when a large database is concerned.
In 2011, to overcome the above drawback, scholars proposed a new type of QPQ, i.e. quantum-key-distribution (QKD)-based QPQ. Based on the mature technology of QKD, this new kind of QPQ has some important advantages such as being easy to realize and loss-tolerant. Therefore, as a practical model, QKD-based QPQ is overwhelmingly attractive and soon becomes a research hotspot.
However, QKD-based QPQ seems somewhat unreliable in the sense that all the existing protocols would fail with a non-zero probability. Besides, the database would generally reveal some additional secrets to the honest user. Even worse, to reduce the failure probability, one must increase the expectation of the number of the revealed secrets, while to protect the security of the
database better, the protocol would be more likely to fail. It seems incompatible to improve the above two disadvantages of the present QKD-based QPQ. Fortunately, based on a differential phase-shift (DPS) QKD protocol, researchers have tactfully and perfectly removed these two obstacles.
The DPS-QKD protocol mentioned above was proposed by Toshihiko Sasaki et al. in the famous journal Nature in 2014. In this QKD protocol participants need not to monitor signal disturbance anymore. It can tolerate up to 50% bit error rate by setting a parameter large enough, while the generally used BB84 protocol can only tolerate 11% at most. Besides, the DPS-QKD protocol is naturally immune to the photon-number-splitting attack, where the adversary utilizes the imperfection of the photon source in practice to attack. As is seen, the technology of DPS has greatly promoted the development of QKD and captured lots of attention. Recently, researchers find that DPS is also beneficial for QKD-based QPQ.
Based on the DPS-QKD, a new QPQ protocol was proposed by Bin Liu, Fei Gao, Wei Huang and Qiaoyan Wen, scientists at the State Key Laboratory of Networking and Switching Technology, Beijing University of Posts and Telecommunications, in the Chinese city of Beijing (See Figure 1). "It maintains the advantages of the QKD-based QPQ, i.e., easy to implement and loss tolerant" according to the four scholars.
In an article connected with College of Computer Science, Chongqing University, in the Chinese city of Chongqing, they revealed in the study, which was published in Science China-Physics, Mechanics & Astronomy, that it is the randomness in the dilution of the oblivious key, one of the main processes in such protocols, that caused the possible failure of previous QKD-based QPQ. And utilizing the features of DPS, their protocol successfully avoids the process of dilution.
Without the process of dilution, this new protocol becomes more reliable and reasonable, compared with the previous QKD-based QPQ protocols. Just as the scholars stated in their article: "Different from the situations in the previous QKD-based QPQ protocols, in our protocol, the number of the items an honest user will obtain is always one and the failure probability is always zero."
They also calculated an upper bound for the leaked information of the database in theory, and claimed that when the number of the database items "become larger, the advantage of our protocol's bound would be highlighted comparing with the other QKD-based QPQ protocols".
What's more, just like the DPS-QKD, the QKD-based QPQ protocol proposed by the four scholars is also naturally immune to the photon-number-splitting attacks. While other QKD-based QPQ protocols would leak more secrets of the database than expected to both the outside adversaries and the dishonest users provided the photon source were not perfect.
At the end of this article, these four scholars summarized "the proposed protocol is the first QKD-based QPQ protocol without the process of the oblivious key dilution, and, therefore, it is the first QKD-based one with no failure probability and no information reveal for the database when the user is honest", and they believed that "the proposed protocol initiates a new branch of QKD-based QPQ".